Penetration Testing
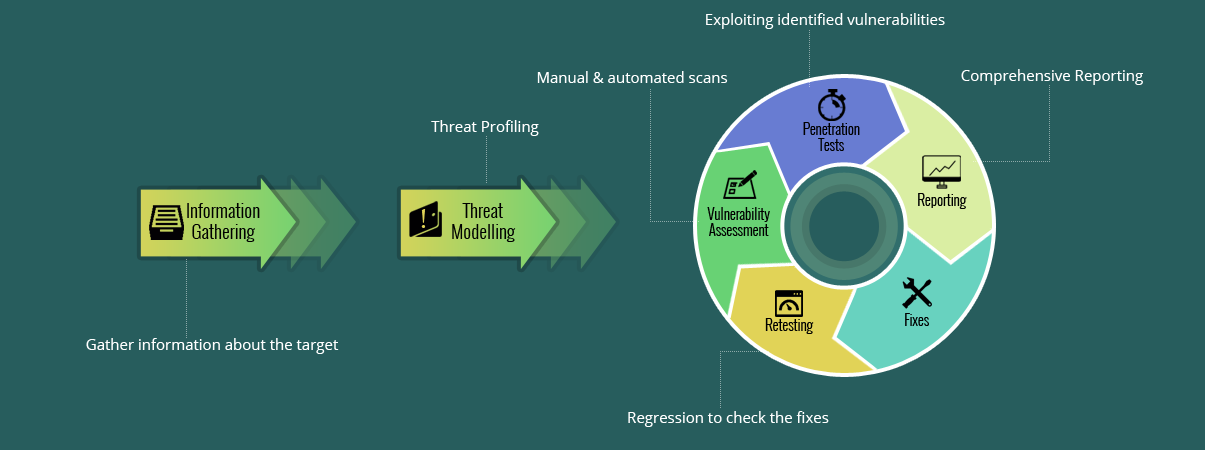
Penetration test or "pentest" for breaking sustainability is a method to evaluate computer systems, networks protection or organization measures by simulating directed attack. The main goal of this test is system vulnerabilities identification, which may appear due to the improper configuration, hardware and software errors, and operational deficiencies in the processes and technical means of control. It is a component of information security audit or can be conducted separately.
All kinds of Pentest approaches are following the same process defined above. During the evaluation of the information security aspects, Auditor will simulate the intruder behavior, trying to pass through the defensive mechanisms of the target infrastructure. The penetration test is performed by highly qualified specialists, which respect the ethical principles while conducting the test. Any data about security found during the pentest are passed to system's owner together with potential impact assessment.
Besides, this Auditor is providing a detailed list of recommendations to remediate identified vulnerabilities.
 NETWORK PENETRATION TESTING
NETWORK PENETRATION TESTING
Network Vulnerability Assessment is searching for the known and potential gaps in Network Protection Infrastructure. Am-Pro is using internationally recognized methodologies of penetration testing, such as:
- Information Systems Security Assessment Framework (OISSG);
- The Open Source Security Methodology Manual (OSSTMM);
- NIST Guideline on Network Security Testing;
- ISACA Switzerland – Testing IT Systems Security With Tiger Teams;
- Cybersecurity Vulnerability Assessment Methodologies (Cybersecurity VAMs).
- OWASP Testing Guide
 APPLICATION PENETRATION TESTING
APPLICATION PENETRATION TESTING
Application Penetration Testing is more precise vulnerability assessment. It is aiming at code weaknesses detected in web applications, APIs and mobile applications both Android and iOS.
- The Open Source Security Methodology Manual (OSSTMM)
- CWE - Common Weakness Enumeration Framework
- OWASP
- OWASP Application Security Verification Standard
- OWASP IOS Application Security Testing
- OWASP Mobile Security Project
- OASAM - Open Android Security Assessment Methodology

Social Engineering Testing
Social Engineering is a very different way of data leaking and information exposure. Despite its complexity and sophistication, this methodology is widely used against businesses and organizations. The main idea is to persuade a specific person to expose the required information. The variety of ways it can be done is limited only by the imagination of the attacker. Our experts have an impressive experience in it.
The common vision of how Social Engineering is working is related to trust that only confiding people can do such mistake. This is not quite correct. The skilled attacker can ensure even the skeptical individuals to see the real truth.
We are helping businesses and organizations to design the flow to protect them from this kind of the threat.
